Have you ever seen one of these weird redirects? WordPress, for example, may refuse to show the log-in page, leaving you out of its admin interface for good. Here is what to do about it.

Cyber security, infotech

Have you ever seen one of these weird redirects? WordPress, for example, may refuse to show the log-in page, leaving you out of its admin interface for good. Here is what to do about it.

Users of PuTTY, the popular SSH client, can transfer PuTTY’s rather extensive settings to another Windows PC by saving them in a registry file and merging the file with the local registry of the other computer, in three easy steps.

Fighting spam, aren’t we all… To stem the tide of unwanted junk mail look no further than the built-in access restrictions in Postfix.

To redirect a subdirectory in NGINX, use this location block (an example for https):
location /old-subdirectory {
return 301 https://$server_name/new-subdirectory/;
}
For more NGINX redirects see this post: RegEx Bliss: Set Up URL Redirects in NGINX Using Regular Expressions without Rewrites.

Mode bits in Linux/Unix have been puzzling newbies to no end:
-rwxrwxrwx. 1 owner group 420 Dec 21 12:46 .bash_history
The first mode bit designates the type of the item; the following nine mode bits indicate access permissions on the item with respect to the owner, the group and all other users.
The first character field is a special file designator. It can indicate that an item is:
For lack of a letter, a leading ‘–‘ in place of a special file designator indicates that the item in question is a regular file.
Each consecutive three characters within the nine permissions bits represent privileges that may be assigned to the owner of an item (the first three characters after the special file designator), the group (the next three characters), and/or everyone else (the next three characters). Unix/Linux supports the following permissions:
For example the following notation:
-rw-r----- someuser somegroup filename
translates as follows:
Unix permissions can be expressed numerically as powers of two:
This designation ensures that there is no room for overlaps. Undefined permissions aren’t possible, either. It’s as clear cut as it gets.
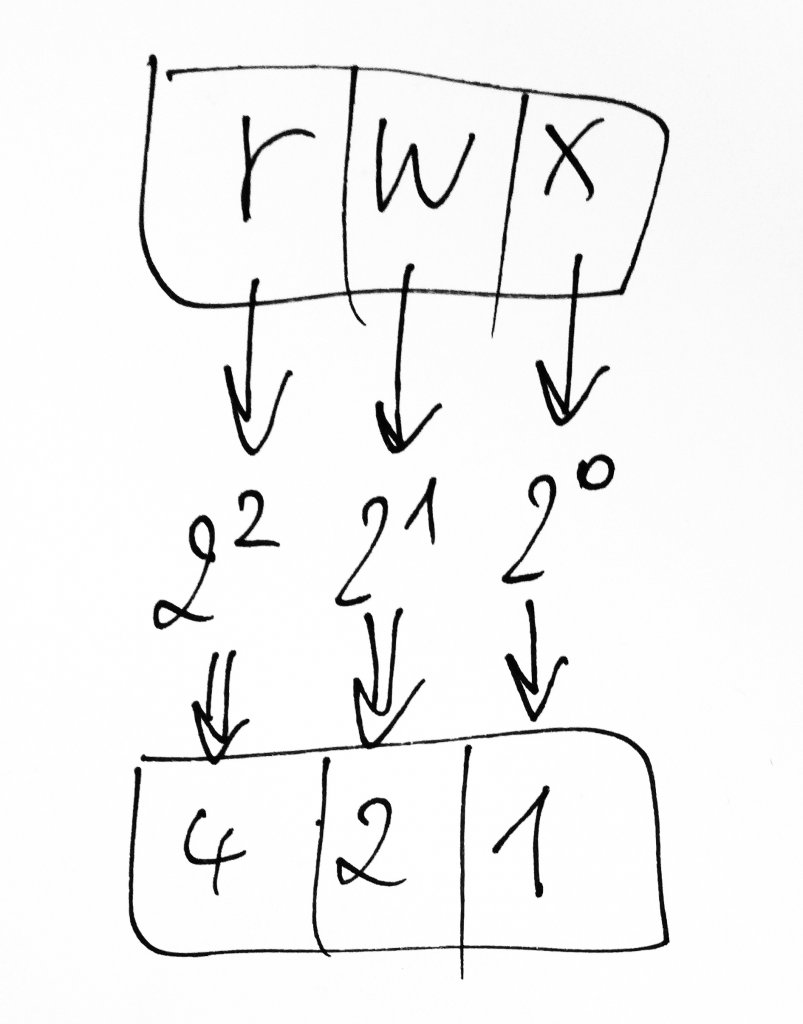
To arrive at a numerical value for permissions that affect an entity class such as the owner, the group or everyone else (meaning all users that neither belong to the group nor own the object), all you have to do is sum up the permissions that represent privileges of this entity class (the owner’s, the group’s, and everyone else’s permissions, one single digit for each class).
If an entity class such as the owner, the group or ‘everyone else’ has read (4), write (2), and execute (1) permissions, these equal 7 (4+2+1=7).
Likewise, if an entity class such as the owner, the group or ‘everyone else’ can read (4) and execute (1) a file but not write (0) to it, the permissions equal 5 (4+0+1=5).
If an entity class such as the owner, the group or ‘everyone else’ has read (4) permissions only, these permissions are represented by the digit 4 (4+0+0=4).
This is how you can change privileges on a file in a way that only grants its owner read, write, and execute permissions:
chmod 700 filename ls -l filename -rwx------ owner group filename
When a new file is created, it usually inherits the group id of its creator. However, there are exceptions from the rule.
If you want new files to inherit the group id of their parent folder, enable the SGID (Set Group ID on execution) bit on that folder.
In addition to the above, the permissions to delete or rename a file or directory can be limited to its owner and the root user by means of setting a sticky bit (mode 1000) in one of two scenarios:
In each case, the sticky bit appears in place of the last one of the three mode bits that denote permissions for “everyone else”.
Following the file mode bits is a single character that specifies an alternate access method such as an access control list. When the character following the file mode bits is a space, there is no alternate access method. When it is a printing character, then there is such a method.
GNU ‘ls’ command uses a dot (‘.‘) to indicate a file with an SELinux security context and no other alternate access method. A file with any other combination of alternate access methods is marked with a ‘+‘ character.
In order to read out the alternate access methods, you can use the command:
getfacl
for example like this:
-rw-------. 1 centos centos 586 Oct 21 15:03 authorized_keys getfacl . # file: . # owner: centos # group: centos user::rwx group::--- other::---
Tip: use this SELinux label for a temp directory
chcon -t tmp_t temp
©2022 CybrAnalytiqa OÜ